As a part of our Server Controlling Services, we assist our customers with a couple of SQL questions reliably.
Today, “Error 17806 Severity 20 State 14”, let us research the hints of this mix-up and its likely courses of action.
SQL error 17806
If we are using Windows approval to interface with a SQL Server in Windows at least 2004, “Error 17806 Severity 20 State 14”, we may encounter the going with error:
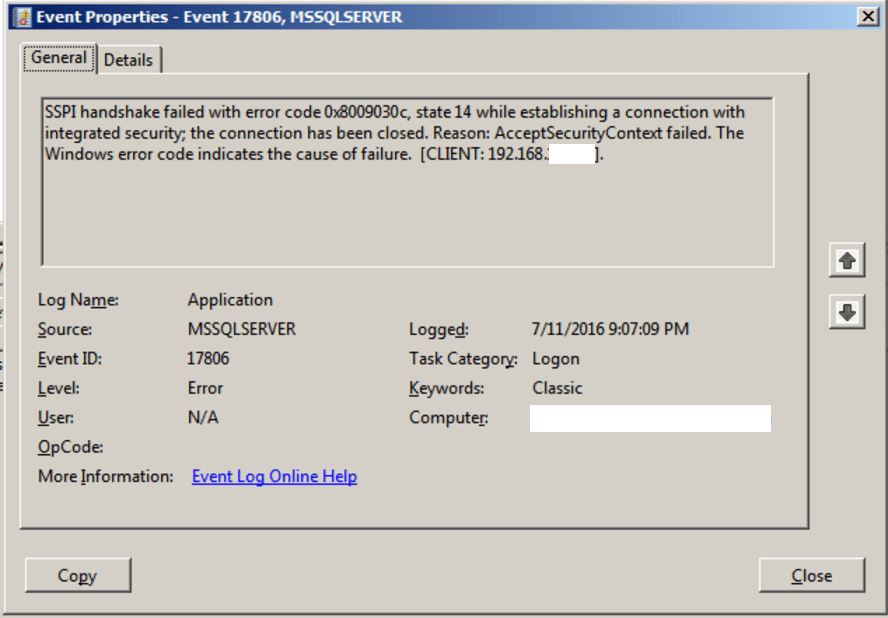
SSPI handshake failed with error code 0x8009030c, state 14 while developing a relationship with consolidated security; the connection has been closed. Reason: Accept Security Context failed. The Windows error code shows the justification for dissatisfaction. The logon tries failed.Mix-up: 17806, Severity: 20, State: 14.
This error can happen due to the Active Directory configuration issue or Network related issues.
In Windows at least 2004, the default method for developing a connection is Kerberos. Regardless, “Error 17806 Severity 20 State 14”, if it misfires, we can set up a connection using NTLM. This may enroll on the SQL Server error log in light of Kerberos blocking.
 What is Kerberos?
What is Kerberos?
Kerberos is a PC network security show that confirms organization requests between somewhere around two trusted in has across an untrusted network, like the web. “Error 17806 Severity 20 State 14”, uses secret-key cryptography and is a trusted outcast for approving client-server applications and confirming customers’ characters.
At first, made by the Massachusetts Institute of Technology (MIT) for Project Athena in the last piece of the ’80s, Kerberos is as of now the default authorization advancement used by Microsoft Windows. “Error 17806 Severity 20 State 14”, Kerberos executions similarly exist for other working systems like Apple OS, FreeBSD, UNIX, and Linux.
Microsoft completed its version of Kerberos in Windows 2000, and it’s transformed into the go-to show for locales and single surrender on performances at different stages. “Error 17806 Severity 20 State 14”, The Kerberos Consortium stays aware of the Kerberos as an open-source project.
How Might It Work?
The show gets its name from the unimaginable three-headed canine Kerberos (in any case called Cerberus) from Greek dreams, the canine guardian to the path to the secret world. “Error 17806 Severity 20 State 14”, Kerberos had a snake tail and a particularly terrible disposition and, paying little mind to one noticeable extraordinary case, was an uncommonly accommodating guard.
However, in the show’s cast, the three heads of Kerberos address the client, the server, and the Key Distribution Center (KDC). The last limits as the accepted untouchable approval organization.
Customers, machines, and organizations that usage Kerberos depend upon the KDC alone, which fills in as a singular connection that gives two limits: confirmation and ticket-permitting. KDC “tickets” offer confirmation to all social events, allowing centers to check their character securely. “Error 17806 Severity 20 State 14”, The Kerberos check process uses a conventional normal secret cryptography that hinders packs connecting the association from being scrutinized or changed, similarly as protecting messages from tuning in and replay (or playback) attacks.
What is Kerberos Used for?
Disregarding the way that Kerberos is found any place in the high-level world, it is used strongly on secure systems that depend upon trustworthy inspecting and confirmation features. “Error 17806 Severity 20 State 14”, Kerberos is used in Posix confirmation, and Active Directory, NFS, and Samba. It’s moreover an elective approval system to SSH, POP, and SMTP.
 As a piece of the learning stream of what Kerberos is, “Error 17806 Severity 20 State 14”, let us next discover concerning the Kerberos show stream.
As a piece of the learning stream of what Kerberos is, “Error 17806 Severity 20 State 14”, let us next discover concerning the Kerberos show stream.
Kerberos Protocol Flow Overview
“Error 17806 Severity 20 State 14”, We have to research what Kerberos approval is and how it works by isolating it into its middle parts.
Here are the fundamental components that are drawn in with the normal Kerberos work process:
- The client follows up in light of a legitimate concern for the customer and starts correspondence for a help interest
- Server. The server has the assistance the customer needs to get to
- Approval Server (AS). The AS plays out the best client approval. In case the confirmation happens viably, the AS issues the client a ticket called TGT (Ticket Granting Ticket). “Error 17806 Severity 20 State 14”, This ticket ensures various servers that the client is stated
- Key Distribution Center (KDC). In a Kerberos environment, the approval server is reasonably separated into three segments: A database (DB), the Authentication Server (AS), and the Ticket Granting Server (TGS). These three areas, consequently, “Error 17806 Severity 20 State 14”, exist in a singular server called the Key Distribution Center
- Ticket Granting Server (TGS). The TGS is an application server that issues organization tickets as an assistance
As of now what about we separate the show stream.
In any case, there are three basic secret keys drawn in with the Kerberos stream. There are fascinating secret keys for the client/customer, “Error 17806 Severity 20 State 14”, the TGS, and the server conferred to the AS.
- Client/customer. Hash got from the customer’s mysterious key
- TGS secret key. Hash of the mysterious key used in choosing the TGS
- Server secret key. Hash of the mysterious expression used to choose the server offering the help.
The show stream involves the going with progress:
Stage 1: Initial client confirmation interest. The customer demands a Ticket Granting Ticket (TGT) from the confirmation server (AS). This sale fuses the client ID.
Stage 2: KDC affirms the client’s confirmations. The AS truly investigates the database for the client and TGS’s openness. If the AS finds the two characteristics, it creates a client/customer secret key, “Error 17806 Severity 20 State 14”, using the customer’s mysterious expression hash.
The AS then processes the TGS secret key and makes a gathering key (SK1) encoded by the client/customer secret key. The AS then makes a TGT containing the client ID, client network address, “Error 17806 Severity 20 State 14”, timestamp, lifetime, and SK1. The TGS secret key then encodes the ticket.
Stage 3: The client translates the message. The client uses the client/customer secret key to translate the message and concentrate the SK1 and TGT, “Error 17806 Severity 20 State 14”, making the authenticator that endorses the client’s TGS.
Stage 4: The client uses TGT to request access. The client requests a ticket from the server offering help by sending the isolated TGT and the made authenticator to TGS.
Stage 5: The KDC makes a ticket for the recording server. The TGS then uses the TGS secret key to unscramble the TGT got from the client and concentrates the SK1. The TGS translates the authenticator and confirms whether it facilitates with the client ID and client network address. “Error 17806 Severity 20 State 14”, The TGS moreover uses the eliminated timestamp to guarantee the TGT hasn’t ended.
Accepting the cycle drives all of the checks viably, the KDC produces a help meeting key (SK2) that is split between the client and the goal server.
Finally, the KDC makes an assist with tagging that fuses the client id, client network address, timestamp, and SK2. “Error 17806 Severity 20 State 14”, This ticket is then encoded with the server’s secret key procured from the DB. The client gets a message containing the assistance ticket and the SK2, all encoded with SK1.
Stage 6: The client uses the report pass to confirm. The client orders the message using SK1 and concentrates SK2. This association makes another authenticator containing the client network address, client ID, “Error 17806 Severity 20 State 14”, and timestamp, encoded with SK2, and sends it and the assistance pass to the goal server.
Stage 7: The target server gets unraveling and confirmation. The target server uses the server’s strange key to unscramble the help ticket and concentrate the SK2. The server uses SK2 to decipher the authenticator, “Error 17806 Severity 20 State 14”, performing checks to guarantee the client ID and client network address from the authenticator and assist with tagging match. The server moreover checks the help pass to check whether it’s ended.
Justification for SQL error 17806
SQL Server engine record running with a Domain organization account, and that record looked at the time a Kerberos connection attempt. “Error 17806 Severity 20 State 14”, The connection would work, but it would kick down to NTLM.
Besieged Kerberos Authentication to connect with SQL Server.
To attest if we have any database connection using Kerberos check, run:
SELECT specific auth_scheme FROM sys.dm_exec_connections
If we simply see NTLM and SQL, there is no Kerberos connection.
To use Kerberos, “Error 17806 Severity 20 State 14”, the client and SQL Server ought to be in a comparative space and a Service Principal Name (SPN) ought to be enlisted with Active Directory for the SQL Server organization account.
We can check if the assistance account at this point has SPN, by running:
setspn - l <domain\sqlserviceaccount>
If we don’t see anything starting with MSSQLSvc\, the record isn’t set up with SPN.
SSPI handshake slip-ups can be a Time/Clock contrast between the client clock shifts server clock.
 Deals with serious consequences regarding SQL error 17806
Deals with serious consequences regarding SQL error 17806
“Error 17806 Severity 20 State 14”, Permit us by and by to focus on specific systems our Expert Planners propose to fix this mix-up.
Procedure 1:
- Go to select beginning – > run… Regedit
- Go to: HKLM\System\CurrentControlSet\Control\LSA
- Then, add DWORD regard “DisableLoopbackCheck”
- Set this value to 1
- Reboot resulting in carrying out this improvement.
By and large, this will impact vault change.
Strategy 2:
Restart the SQL program organizations.
Strategy 3:
- Reboot the getting into naughtiness Domain Controller
- Right Client to Server time
- Make an SPN for the SQL server.
We can genuinely select SPN as a Domain Administrator.
To make an SPN for the NetBIOS name of the SQL Server we use the going with a request:
setspn – A MSSQLSvc/<SQL Server PC name>:1433 <Domain\Account>
To make an SPN for the FQDN of the SQL Server we use the going with a request:
setspn - A MSSQLSvc/<SQL Server FQDN>:1433 <Domain\Account>
If SQL Server organization account grants “Permitted write to help boss name” advantage in Active Directory, “Error 17806 Severity 20 State 14”, SQL Server database engine will select itself when it starts and unregisters at a conclusion.
If the Domain Administrators don’t permit this setting, we should truly enroll the SPN and the SSPI slip-up will vanish.
Still, the SQL Server organization record ought to yield a “Record is trusted for task” advantage in Active Directory. If the SQL Server interfaces with another SQL Server using Linked Server, “Error 17806 Severity 20 State 14”, the server ought to similarly surrender “Trust this PC for the arrangement to any help” advantage.
For a named event, we can use the FQDN of the named event instead of SQL Server FQDN and use the port number.
For a gathered server, we ought to use the FQDN of the SQL Server virtual name. For the present circumstance, “Error 17806 Severity 20 State 14”, we will require two entries, one with port name and one without, for instance,
setspn - A MSSQLSvc/<Virtual SQL Server FQDN> <Domain\Account>setspn - A MSSQLSvc/<Virtual SQL Server FQDN>:1433 <Domain\Account>
Kerberos approval works when SQL Server, Service Account and Windows account getting to the SQL Server are incomparable windows region.
Conclusion
In this way, SQL error 17806 happen on account of Active Directory course of action issue or Network issues. Today, “Error 17806 Severity 20 State 14”, we saw a couple of techniques our Support Techs found the best fit to address this error.