OCSP stapling is a TLS/SSL development that plans to chip away at the introduction of the SSL course of action while staying aware of visitor security. Before continuing with the arrangement. A short brief on how announcement denial capacities.
Around here at ARZHOST, we have considered a couple of such Apache-related requests to be essential for our Server Management Services for the web has and online expert associations.
“Unable to Configure Certificate for OCSP Stapling” Today, we’ll examine how to plan OCSP stapling on Apache.
What is OCSP and how might it work?
OCSP addresses Online Certificate Status Protocol and is used by Certificate Authorities to truly check out the disclaimer status of an X.509 mechanized underwriting. In this blog, we react to certainly the most typical requests in regards to OCSP including how it works. “Unable to Configure Certificate for OCSP Stapling” The positions of confirmation trained professionals and confirmation authorization subject matter experts. How to look at supports through a CRL.
How does OCSP Work?
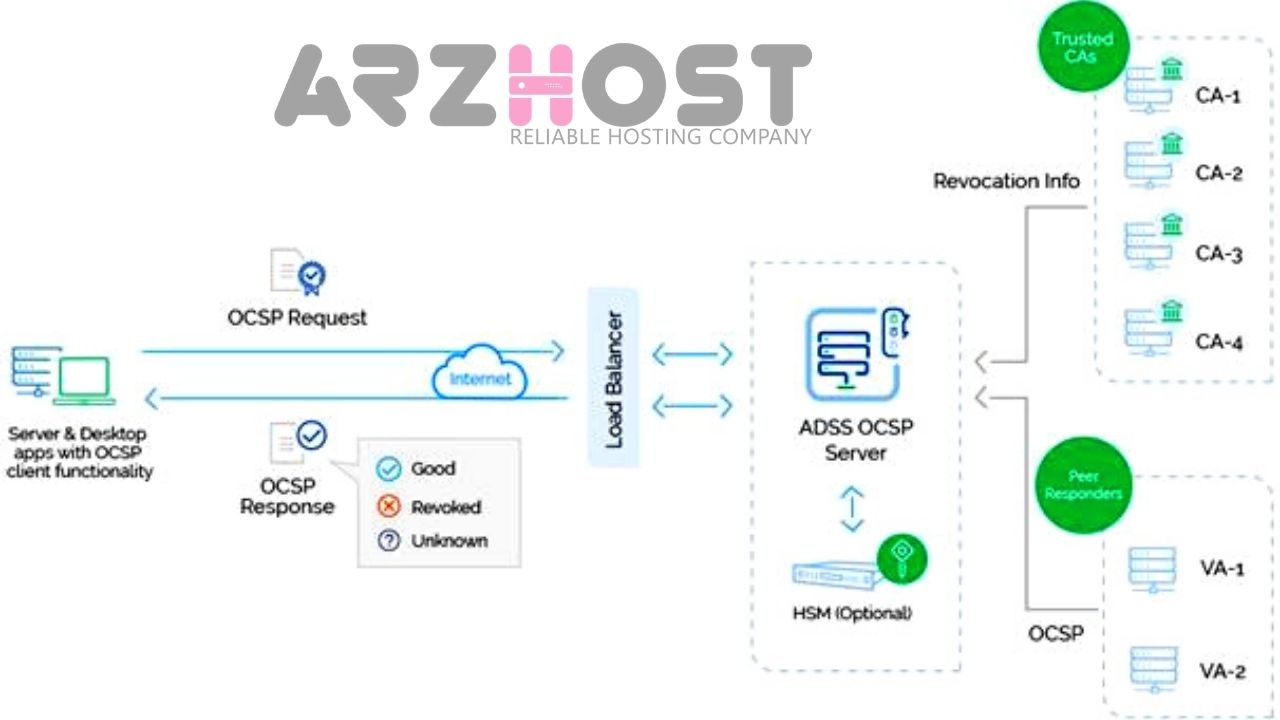
Right when a customer requests the validity of a confirmation. An OCSP request is transported off an OCSP Responder. This checks the specific supporting with an accepted confirmation authority and an OCSP response is sent back with a response of either 'incredible', 'denied', or 'dark'.
How does OCSP Stapling Works?
- Most importantly, the webserver working with the SSL support sends an inquiry to the capable CA’s server.
- Then, at that point, the capable CA’s server responds with the OCSP status and a time stamp.
- Beginning here, whenever a client relates the server staples the OCSP response to the underwriting when it’s presented during the handshake.
- The client confirms the imprint on the time stamp to promise it came from the capable CA.
Expecting that there is an issue. “Unable to Configure Certificate for OCSP Stapling” The client’s program gives an error message.
What is a supporting authority and how might they work?
Support Authorities (CA) are a focal point of an automatic trust structure that issues and administers progressed confirmations which can be used to look at the personality of public key subjects. License Authorities are sent as a part of a connection’s IT security plan and worked by inside security gatherings or are worked by Trust Service Providers (TSPs).
Assertion Authorities use the Public Key Infrastructure (PKI) X.509 verification to confirm whether public keys match the personality of the customer. The high-level confirmations contain:
- The owner’s name
- The owner’s public key
- The capable CA’s name
- Validation Validity Dates
(significant from, authentic to) - Extra optional information
(for instance what the validation can be used for, where to investigate the denial status of the presentations, etc)
Confirmation Authorities carefully sign the above data to hinder further change. CAS uses their private key to sign progressed supports and anyone with the CA’s public key can support the imprint on a modernized verification. Accepting the information as it can’t be changed. The claim of the server character is key so to securing a high-level confirmation from a Certificate Authority.
You are expected to give a check of character. Either eye to eye or through web-based individual examinations. “Unable to Configure Certificate for OCSP Stapling” before an announcement can be given. In the EU, eIDAS guaranteed CAs are known as Qualified Certificate Authorities and are worked by Capable Trust Service Providers.
What is a validation certification authority?
ADSS OCSP Server is a significant level x.509 statement Validation Authority server that adjusts to the IETF RFC 6960 standard, is FIPS 201 Certified (APL #1411) and upheld for use by US government associations for HSPD-12 effecting. The ADSS OCSP Server is an awesome confirmation community course of action fit for giving OCSP confirmation authorization organizations to various Certificate Authorities (CAs) at the same time.
Fundamental or refined confirmation approaches are maintained for each individual. CA and ADSS OCSP Server give an organized evident record of all skills alongside an easy-to-use OCSP requesting and response watcher. “Unable to Configure Certificate for OCSP Stapling” This is major for charging just as exploring inside managed organization systems or undertaking structures.
How should I take a look at my CRL announcement?
CRL addresses Certificate Revocation List. CRLs contain a once-over of rejected automatic confirmations from validation subject matter experts. Validations can be rejected for different reasons someone may have uncovered their smartcard or USB token as lost. A guarantor may have left the association and isn’t, by and large, supported to sign, or the confirmation may have been compromised. Progressed confirmations on a CRL should buy and don’t be trusted.
CRLs gives a method for admitting the condition with electronic supports by adding surprise ongoing numbers to a once-over that is stamped and stayed aware of by a Certification Authority. These overviews fill in greater associations and put resources into a few chances for clients to download while taking a gander at denial. OCSP offers more vital productivities over CRLs for greater associations.
OCSP servers consume CRLs to offer a hint of whether the backing was denied in this model the OCSP has to empower the CRL on a plan to promise it is giving groundbreaking renouncement information. “Unable to Configure Certificate for OCSP Stapling” Advanced OCSP things provide the ability to the OCSP to examine a CA's database directly. This gives persistent rejection and confirmation whitelisting.
Funding whitelisting gives additional confirmation to end components and confirms that the CA truly gave the statement. Equally, with CRL checking, OCSP requests contain fewer data so are more direct for associations to manage as structures don’t have to download. The latest summary of each rejected signature whenever a confirmation is checked.
Guidelines to enable OCSP stapling on Apache
“Unable to Configure Certificate for OCSP Stapling” As of now could we see how our Hosting Expert Planners engage OCSP stapling on Apache.
1: Check for OCSP stapling support on Apache
“Unable to Configure Certificate for OCSP Stapling” OCSP stapling is maintained on Apache HTTP Server where structure >=2.3.3
We run the going with the request to truly investigate the variation of the apache foundation.
apache2 - vhttpd - v
2: Improve the CA bunch
As of now, we improve the root CA and moderate CA’s underwriting in the PEM plan. Then, we save them in a single archive. “Unable to Configure Certificate for OCSP Stapling” This is for StartSSL’s Root and Intermediate CA announcements.
plate, etc/SSLwget - O - https://www.example.com/certs/ca.pem https://www.example.com/certs/sub.class1.server.ca.pem | tee - a ca-certs.pem>/dev/invalid
Accepting the CA gives validations in the DER plan then we convert them to PEM. For example, DigiCert gives validations in the DER plan. To download them and convert them to PEM we run the going with orders:
plate, etc/SSLwget - O - https://www.example.com/CACerts/HighAssuranceEVRootCA.crt | openssl x509 - enlighten DER - out form PEM | tee - a ca-certs.pem>/dev/invalidwget - O - https://www.example.com/CACerts/HighAssuranceEVCA-1.crt | openssl x509 - enlighten DER - out form PEM | tee - a ca-certs.pem>/dev/invalid (for more help/www.arzhost.com/ssl/hosting/authorities.
3: Organizing OCSP Stapling on Apache
As of now, we will arrange the OCSP stapling. In any case, we modify the SSL virtual hosts record by running the under request.
sudo nano, etc/apache2/districts engaged/example.com-SSL. Conf
Then, we place these lines inside the <virtual Host></virtual Host> order:
SSL CA Certificate File, etc/SSL/ca-certs.pemSSL Use Stapling on
Moreover, we validate a store region outside <Virtual Host></virtual Host> in a comparable record:
SSL Stapling Cache shmcb:/tmp/stapling_cache (128000)
Then, “Unable to Configure Certificate for OCSP Stapling” we do a config test to check for errors:
apachectl - t
Starting there forward. We reload accepting Syntax OK is shown:
4: Organization apache2 reload
We access the site on IE (on Vista or more) or Firefox 26+ and check the slip-up log:
tail/var/log/apache2/error.log
If the record portrayed in the SSL CA Certificate File request is feeling the deficiency of, a presentation a mix-up like coming up next is shown:
[Fri Jan 08 23:36:44.055900 2021] [ssl: error] [pid 1491: tid 139921007208320] AH02217: ssl_stapling_init_cert: Can't improve supporter underwriting![Fri Jan 08 23:36:44.056018 2021] [ssl: error] [pid 1491: tid 139921007208320] AH02235: Unable to plan server support for stapling
“Unable to Configure Certificate for OCSP Stapling” Expecting that no such errors are shown proceed to the last development.
5: Testing OCSP Stapling
Finally, we test accepting the OCSP stapling is working or not by running the under request:
resonation QUIT | openssl client - partner ARZHOST.com:443 - status 2>/dev/invalid | grep - A 17 'OCSP response:' | grep - B 17 'Next Update'
“Unable to Configure Certificate for OCSP Stapling” The aftereffect of the above request will explain if the webserver responded with OCSP data.
Assumptions
Today at arzhost.com, we saw how our Hosting Expert Planners plan OCSP stapling on the Apache server. “Unable to Configure Certificate for OCSP Stapling” This article will guide you on the most ideal way to plan OCSP stapling on the Apache server.
Unable to Configure Certificate for OCSP Stapling” To Check if #OCSP #stapling is engaged:
Go to https://www.arzhost.com/help and in the Server Address box, type in your server address. Accepting OCSP stapling is enabled, under #SSL Certificate has not been denied, aside from OCSP Staple, it says Good.
To Configure your Apache server to use OCSP Stapling:
Modify your site's #virtual Host SSL course of action.Add the going with line INSIDE the <virtual Host></virtual Host> block: SSLUseStapling on.Check the plan for errors with the Apache Control organization. Apachectl - t.Reload the Apache organization. organization apache2 reload.
Some FAQS Related This Article
Question # 1: For what reason is OCSP utilized?
Answer: OCSP is used to take a look at the refusal status of X509 verifications. OCSP gives essential status on authentications progressively and is helpful in time-touchy circumstances like bank exchanges and stock exchanges.
Question # 2: What are OCSP and CRL?
Answer: Endorsement Revocation List (CRL). A CRL is a rundown of denied testaments that are downloaded from the Certificate Authority (CA). Online Certificate Status Protocol (OCSP). An OCSP is a convention for checking repudiation of a solitary testament intelligently utilizing a web-based help called an OCSP responder.
Question # 3: What is OCSP URL?
Answer: The Online Certificate Status Protocol (OCSP) URL application definition field decides if this application utilizes an overall OCSP responder to send demands during declaration approval for end substance authentications. HTTP is the main upheld URL convention; thusly, this worth should start with "HTTP://". ...
Question # 4: What is the CRL convincing point?
Answer: A CRL appropriation point (CDP) is an area on an LDAP registry server or Web server where a CA distributes CRLs. The framework downloads CRL data from the CDP at the stretch indicated in the CRL. At the span that you determine during CRL arrangement, and when you physically download the CRL.