A top cybersecurity objective is eliminating vulnerabilities from systems and applications. Companies use a variety of methods to find software bugs, but no testing methodology offers a more thorough and realistic examination What is Penetration Testing?
An introduction to What is Penetration Testing? is provided in this article. Continue reading to find out how pen testing functions and how businesses use them to stop costly and devastating breaches.
Definition of Penetration Testing
A computer system, network, or application is tested for security flaws during penetration testing (also known as pen testing), a simulation of a cyberattack. These tests rely on a variety of instruments and methods that actual hackers would employ to compromise a company.
White hat attacks and ethical hacking are two other terms for penetration testing.
Pen testers often combine manual testing techniques with automation testing tools to mimic an attack. Penetration tools are also used by testers to scan systems and evaluate the findings.
An effective penetration testing tool ought to:
- be simple to set up and use.
- Be quick when scanning systems.
- Sort flaws according to their seriousness.
- Automate the process of checking for weaknesses.
- Verify past actions again.
- Give thorough reports and logs.
Finding security issues with operating systems, services, applications, configurations, and user behavior is the main goal of a pen test. Using this method of testing, a team can learn:
- Security holes and system weaknesses.
- Regulations governing data privacy and security are not being followed (PCI, HIPAA, GDPR, etc.)
- Team wide lack of security knowledge
- threats identification protocols have flaws.
- The incident response strategy could use some work.
- The security policy has mistaken.
Companies frequently use outside contractors to conduct pen testing. A third-party tester can be more comprehensive and creative than in-house developers because they are less familiar with the technology. Some businesses also offer “bounty” schemes that entice independent contractors to hack networks in exchange for payments if they succeed.
What Happens After a Penetration Test?
The pen test report is the final product of a penetration test. IT and network system managers are informed of the vulnerabilities and exploits by a report. A report should outline how to address the problems and strengthen system defences.
What is Penetration Testing? Every pen test report must to contain:
- A succinct summary: A high-level summary of the test is provided in the summary. The summary can be used by non-technical readers to learn more about the security issues the pen test exposed.
- Utensils, techniques, and Vectors: The test’s instruments and procedures are covered in this section. Additionally, testers describe the precise attack techniques that resulted in a successful breach.
- Detailed results: The security risks, flaws, dangers, and issues that the penetration test uncovered are all listed in this section. This section of the study, in contrast to the executive summary, delves further into technical specifics.
- Recommendations: The part that offers advice describes how to strengthen security and defend the system against actual cyberattacks.
How Frequently Should Penetration Tests Be Performed?
Penetration tests are frequently performed by businesses, typically once a year. A corporation should conduct a pen test in addition to its annual testing anytime the team:
- additional network infrastructure is added.
- instals fresh programmes.
- infrastructure or application modifications or upgrades that are significant.
- opens a new office at a new place.
- new security fixes are added.
- alterations are made to end-user policies.
Running a penetration test after every change the team makes might not be feasible, depending on the size and financial constraints of your business. The team should then employ a mix of vulnerability scanning and penetration tests.
Automated vulnerability scans are speedier and less expensive than pen testing, however they are less effective.
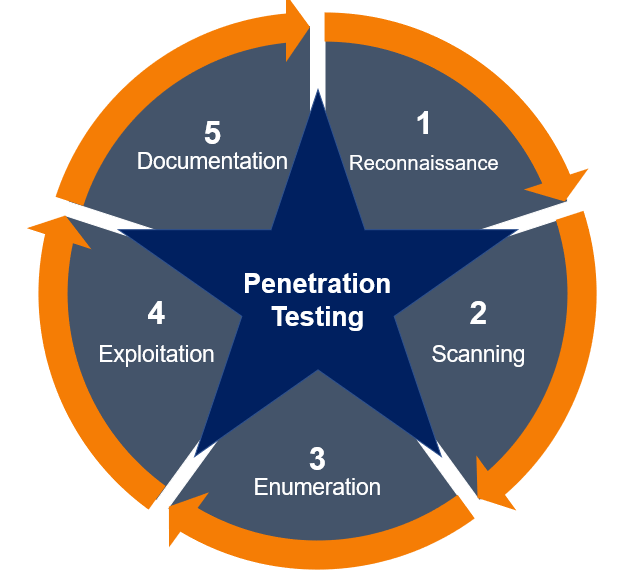
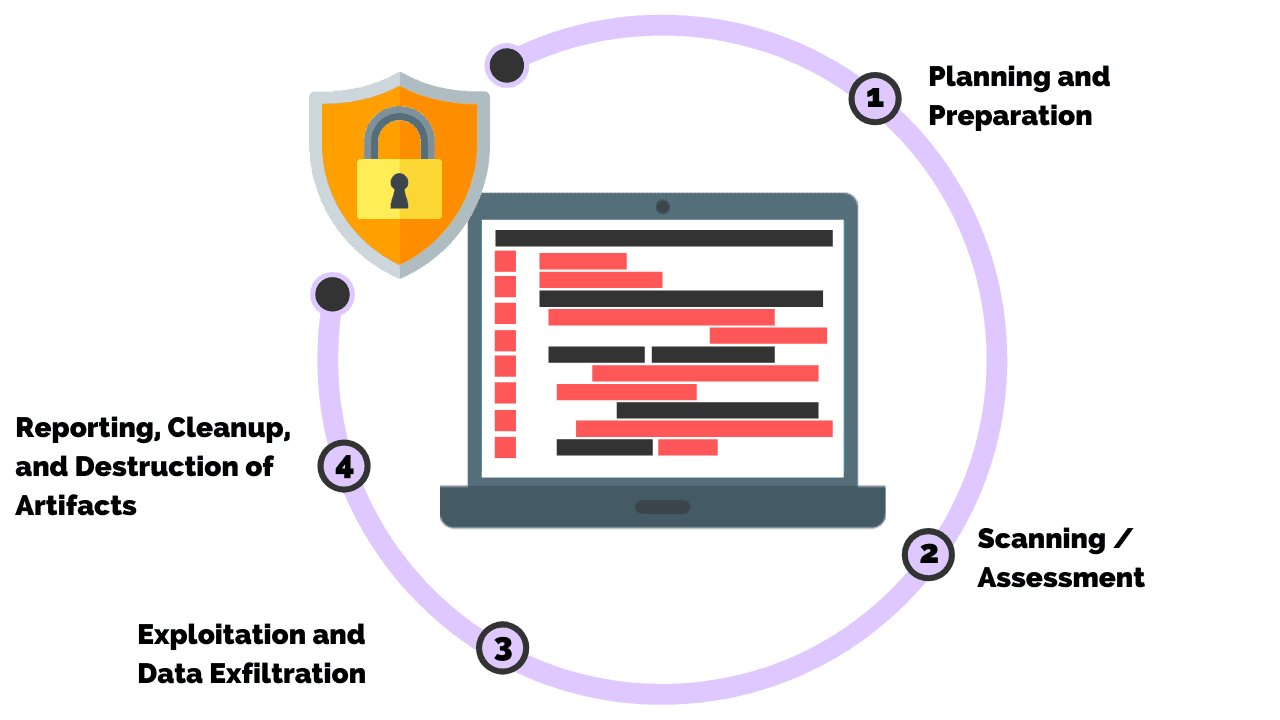
Steps for Penetration Testing
The process of penetration testing is intricate and comprises multiple stages. Here’s a detailed look at each step a pen test takes to examine a target system.
- Penetration Testing Scope
- Reconnaissance (intelligence gathering)
- Threat modeling
- Exploitation
- Post-exploitation
- Analysis and reporting
- Re-testing
1: Scope of Penetration Testing
This stage entails getting ready for the test in advance. The group ought to:
- Describe the test’s logistics.
- Specify the testing area.
- Specify your goals.
- Define goals.
- Set the penetration team’s maximum level of aggression.
- Think about any potential legal repercussions.
2: Reconnaissance (Intelligence Gathering) (Intelligence Gathering)
During the information gathering phase, hackers begin to become familiar with the system and search for prospective entry points. The team must first acquire background data on the subject at this phase, although testers might also identify obvious flaws.
The scanning process is part of the investigation step:
- all the equipment
- the wireless and local networks.
- Firewalls
- applicable applications.
- Websites
- cloud-based technologies.
- employee conduct and procedures.
Open-source intelligence (OSINT) gathering is another phrase frequently used to describe the reconnaissance phase.
3: Modeling of Threats
The testers create unique threats to breach the system using the knowledge gained during the reconnaissance phase. Additionally, the team discovers and groups various assets for testing.
4: Exploitation
Through the access points they discovered in earlier stages, testers try to enter the target. Testers try to increase their access rights if they manage to break into the system.
Pen testers can recognize the following by navigating laterally around the system:
- Bad network segmentation configurations.
- Access to resources and sensitive information.
- Weak password and account management.
5: Post-Exploitation
Pen testers assess the potential damage that a hacker could do by taking advantage of flaws in the system. The testers must decide how the security team should respond to the test breach during the post-exploitation phase.
6: Analysis, Reporting, and Developing Protective Actions
What is Penetration Testing? Testers assemble the test findings into a report that includes the following information:
- The breakdown of hacker activities step by step.
- the gaps and openings that were found.
- The data that the testers could access.
- how long the testers were able to operate outside of detection.
- the actions the business must take to close gaps in security and guard against actual assaults.
7: Re-Testing
The system is prepared for retesting once the security team has implemented the pen report’s improvements. To determine whether the target can now withstand the breach attempt, the testers should rerun the identical simulated attacks.
Methodologies for Standardized Penetration Testing
What is Penetration Testing? The five widely used penetration testing techniques—OWASP, OSSTMM, ISSAF, PTES, and NIST—are usually used by businesses.
1: OWASP
A framework for locating application vulnerabilities is called OWASP (Open Web Application Security Project). Using this technique, a group can:
- Recognize weaknesses in mobile and online applications.
- Identify shortcomings in development methods.
In order to save time and organize problems, the OWASP also gives testers the ability to grade risks. There is no scarcity of OWASP publications, strategies, tools, and technologies because this framework has a big user base.
2: OSSTMM
For network penetration testing, the OSSTMM (Open-Source Security Testing Methodology Manual) uses a methodical scientific approach. For ethical hacking, this peer-reviewed paradigm accurately characterizes operation security.
Pen testers can carry out specialized tests that are tailored to the organizational demands in terms of technology thanks to the OSSTMM.
3: ISSAF
Testing is done with the help of the ISSAF (Information System Security Assessment Framework), which offers a specialized and organized method.
This framework is perfect for testers that want to carefully plan and record each stage of the pen test. Because you may associate each phase with a particular tool, the ISSAF is also helpful for testers who use a variety of tools.
4: PTES
A highly organized seven-step testing methodology is provided by the PTES (Penetration Testing Methodologies and Standards). From reconnaissance and information collecting to post-exploitation and reporting, this technique leads testers through every phase of penetration testing.
To conduct successful tests, PTES requires testers to be familiar with the organization’s procedures.
5: NIST
To enhance overall cybersecurity, the National Institute of Standards and Technology (NIST) provides exact penetration testing criteria. High-risk industries including banking, communications, and energy frequently use this paradigm.
The NIST is frequently a regulatory necessity for American companies. A business must perform penetration testing on networks and applications to be in compliance with the NIST.
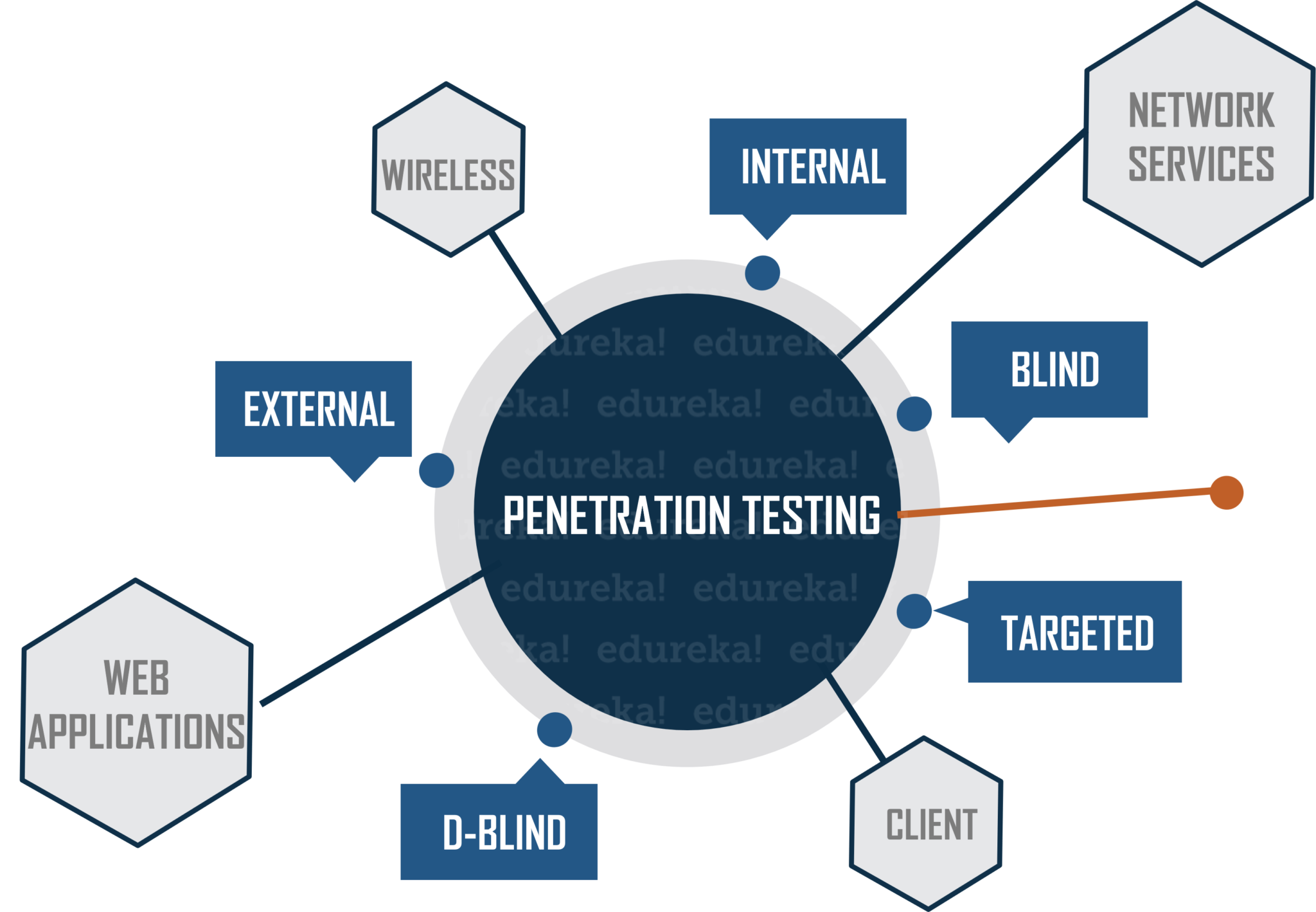
Penetration Testing Types
What is Penetration Testing? The environment, targets, and purposes of penetration tests vary. The company gives the testers various levels of system information depending on the test scenario. The security team may occasionally lack sufficient expertise of the exam.
1: Testing for Black Box Penetration
In a black box test, the penetration team is in the dark regarding the target system. The hackers must enter the system on their own and devise a strategy for a breach.
In a black box test, the testers typically begin with simply knowing the name of the company. This type of testing takes a lot of time because the infiltration team must begin with thorough reconnaissance.
2: Testing for Grey Box Penetration
The testing group is aware of a user with high privileges. The hacker is aware of:
- the architecture and design of the documentation.
- Internal components
The team can concentrate on the targets with the highest risk and value right away with the use of a grey box pen test. Testing of this kind is excellent for simulating an attacker with continuous access to the network.
3: Testing White Box Penetration
Before they begin their work, pen testers are familiar with the target system. This data may consist of:
- IP numbers.
- Schematics of the network infrastructure.
- user guidelines.
- System relics (source code, binaries, containers).
Testers may even have access to the servers that are powering the system, depending on the configuration. White box testing is quick and inexpensive to set up, albeit it is not as authentic as black box testing.
4: Specific Testing
To conduct focused testing, the testing team collaborates with the company’s IT employees. Security professionals and testers are always aware of one another’s activities.
The “lights turned on” approach is another name for focused testing because it is open to all participants.
5: External Evaluation
External testing mimics an assault on devices or servers that are visible from the outside. Typical objectives for outside testing include:
- Name servers for domains (DNS).
- Web-based software.
- Message servers
- Websites
- Application and web servers.
- Firewalls
To determine whether an outside attacker can access the system is the goal of external testing. The secondary goal is to determine how far the attacker can advance following a breach.
Internal Evaluation
Internal testing simulates a firewall-bound insider threat. A user with standard access privileges serves as the default starting point for this test. The following two situations are typical:
- An unhappy worker who made the decision to compromise the system.
- A hacker who used phishing to gain access to the system.
The best way to find out how much harm a malevolent or compromised employee can cause to the system is through internal testing.
Blind Evaluation
Blind testing imitates an actual assault. Although the security team is aware of the test, little is known about the tester’s activities or the intrusion approach.
Testing with two blinds
Only one or two people within the firm are aware of the planned test in a double-blind scenario. Double-blind testing work well when evaluating
- Security surveillance programmes.
- Protocols for incident identification.
- Response techniques.
A double-blind test offers a realistic glimpse into the security team’s capacity to recognize and react to an actual attack.
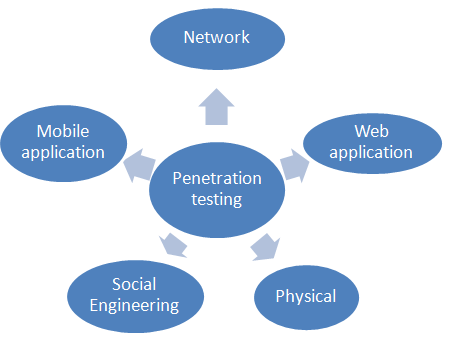
Methods for Penetration Testing (Areas of Testing)
What is Penetration Testing? The various penetration testing techniques you can use to evaluate your company’s defences are listed below.
1: Network Exploitation and Penetration Testing
Network penetration testing imitates hacking methods to compromise hosts, switches, routers, and networks.
This kind of testing comprises:
- Firewall evasion
- avoiding a modern intrusion detection system (NGIPS).
- testing of routers and proxy servers.
- Avoiding IPS and DPS.
- scan open ports.
- security breaches of SSH.
- testing out regulations that prevent lateral movement
- traffic eavesdropping on networks.
- finding out about third-party appliances and old hardware.
This kind of testing involves exploiting both internal and external networks. The following are typical weak spots found through network penetration:
- faulty equipment
- vulnerabilities specific to a product.
- flaws in wireless networks.
- errant services
- weak password security measures.
The most typical kind of pen test involves simulating an assault on the network infrastructure of a company.
2: Tests for Web Application Security
Server-side apps are examined during application security tests for potential vulnerabilities. Typical test subjects include:
- Web-based software.
- mobile apps.
- APIs
- Connections
- Frameworks
These are typical application vulnerabilities:
- scripting and cross-site request forgery.
- injection errors
- poor session administration.
- direct object references that are not safe.
- Coding mistakes.
- Authentication or authorization mechanisms that are not working
- weak encryption.
3: Website and Wireless Network Client-Side
This kind of testing looks for weaknesses in wireless infrastructures and devices. Insecure wireless network setups and inadequate authentication checks are found via a wireless pen test.
This kind of examination include scanning for:
- Errors with web server setting.
- DDoS and anti-malware defences tactics.
- injections of SQL.
- MAC address forgery
- Media players and software for producing content.
- site-to-site scripting
- access points and hotspots.
- encrypting procedures.
4: Attacks through Social Engineering
Social engineering tests look for weaknesses in staff behavior and protocols. A social engineering assault can result in compromised credentials, malware, ransomware, or unlawful access.
Social engineering mock attacks frequently resemble actual assaults like:
- Eavesdropping
- Tailgating
- Phishing assaults
- Spear-phishing.
- Baiting
- Scareware
- Pretexting
5: Physical Evaluation
Physical penetration tests aim to physically enter commercial spaces. This type of testing guarantees the reliability of:
- RFID technology.
- Cameras
- Keypads and entry systems for doors.
- behavior of vendors and employees.
- sensors for light and motion.
Hackers frequently combine social engineering techniques with physical tests to produce realistic attack scenarios.
6: Testing of cloud pens
The defences guarding cloud assets are investigated during cloud penetration testing. Pen tests find possible vulnerabilities in cloud-based apps, networks, and setups that could give hackers access to:
- Company identification.
- Internal mechanisms.
- Sensible information
For businesses that rely on IaaS, PaaS, and SaaS technologies, this kind of testing is crucial. Cloud pen testing is crucial for making sure that cloud implementations are secure.
Final Words
A business can use penetration tests to proactively identify system flaws before hackers have a chance to cause harm. Run simulated attacks on your systems on a regular basis to maintain IT security and avoid expensive breaches.