All networked communication is made possible by the Domain Name System (DNS). What are Some Best Practices When Creating Internal DNS Namespaces? When something goes wrong, DNS may appear to be an invisible force or entity, but it soon becomes clear that nothing can function without it.
The finest techniques and the most essential security precautions to maintain the health of your DNS infrastructure are outlined in this article.
To create a reliable and secure DNS, make carefully consider the factors stated below.
Best Practices for DNS Performance
Make sure DNS is highly available and redundant. The DNS infrastructure needs to be highly available because DNS is the foundation of network applications.
You must have at least the primary and secondary DNS servers in your business in order to achieve the necessary redundancy. Having at least two internal DNS servers is necessary to maintain the business-critical services in operation.
All email, file-sharing, and active directory services depend on reliable DNS performance. Internal DNS servers are required for proper internal device communication. When one DNS server encounters a problem, the other one takes over right away.
When the primary DNS server is down, administrators configure their devices to use the secondary DNS automatically. Any address inside a private network’s IP range can act as the internal DNS server’s IP address.
You can achieve high availability of the DNS infrastructure by creating redundant DNS servers. Your DNS records will remain in sync and secure from failures thanks to continuous replication from primary to secondary servers. You can be guaranteed that there will never be a time when an end-user is without access to services.
DNS servers and other DNS data should be hidden
What are Some Best Practices When Creating Internal DNS Namespaces? Not all users must have access to every DNS server or every piece of data.
Start by making only the servers and the information required for those utilizing them accessible. This is crucial if you require the public to be able to see your domain names.
Next, conceal your main DNS server. External users must not be able to see primary servers. There shouldn’t be any publicly accessible name server databases that include the data for these servers. Requests from end users should only be handled by secondary DNS servers.
A DNS server must be an authoritative-only DNS server if it is reachable from outside your network. External users are not required to query your recursive DNS servers. A high-performance configuration involves a server only responding to iterative queries for the specific zones for which it is the authoritative server.
Finally, the main servers in your company should only be accessible by system administrators and IT staff. All internal users may have access to your principal DNS servers, which could pose a serious security risk. As a general rule, keep the DNS servers and the information out of the reach of people.
Use an internal or external DNS server or both?
The internal configuration affects the response to this query. You must direct devices to an internal DNS server in order to enable communication across devices on the same domain. Internal device hostnames cannot be resolved by external DNS servers.
For instance, only an internal DNS can deliver a resource record when a computer DESKTOP1 submits a DNS query for an office printer or a server hr-1. You won’t be able to use internal resources if you configure a device to use an external DNS, like Google’s 8.8.8.8, for example.
You must establish the primary and secondary DNS in internal environments to an internal name server. There won’t be any connectivity problems, not even if the main DNS server crashes.
All records are stored on the backup secondary DNS server. Whenever there is a problem, this server answers to all requests until the primary server is operational again.
Use the neighborhood or nearby DNS server
There are frequent offices for large companies all over the world. Every office needs a local DNS server, which you should install if the infrastructure permits.
The explanation is that a local server speeds up DNS request responses. A user experiences slower load times when a query goes over a wide area network to a distant name server.
The quantity of DNS queries increases with a large number of clients. All requests can be serviced by a centralized group of DNS servers, but with increased latency. Response times are minimized by pointing users’ computers at the nearest or closest name server.
The maximum latency in this situation is 50ms. Furthermore, the actual number is frequently substantially lower. All machines load faster when the closest DNS server is used. By doing this, you relieve some of the strain on the remote server at headquarters and enhance its functionality. Here as well, the advice to run at least two DNS servers is still valid.
DNS Security Guidelines
Cyberattacks frequently target DNS servers. What are Some Best Practices When Creating Internal DNS Namespaces? One of the most important steps in preventing breaches in your organization is to secure DNS infrastructure.
Make careful to implement the security steps listed below to prevent a significant impact on your DNS setup:
1: Turn on DNS logging
The most effective technique to keep track of DNS activities is through DNS logging. You can tell whether someone is tampering with your DNS servers by looking at the logs. Debug logs can let you know whether there are problems with DNS queries or updates in addition to client activities.
DNS logs also display cache poisoning evidence. In this instance, an attacker modifies the data kept in the cache and diverts clients. An IP address for www.youtube.com, for instance, may be changed to an IP address for a malicious website.
Now, when a client requests information from DNS for youtube.com, the server responds with the incorrect IP. When users access websites they didn’t intend to, hackers can target them.
Despite the fact that DNS debug logging increases security, some system administrators opt to disable it. Performance improvement is the primary justification. You can spot some attacks, like DDoS, by keeping an eye on network traffic, but not cache poisoning. Consequently, we strongly advise turning on DNS.
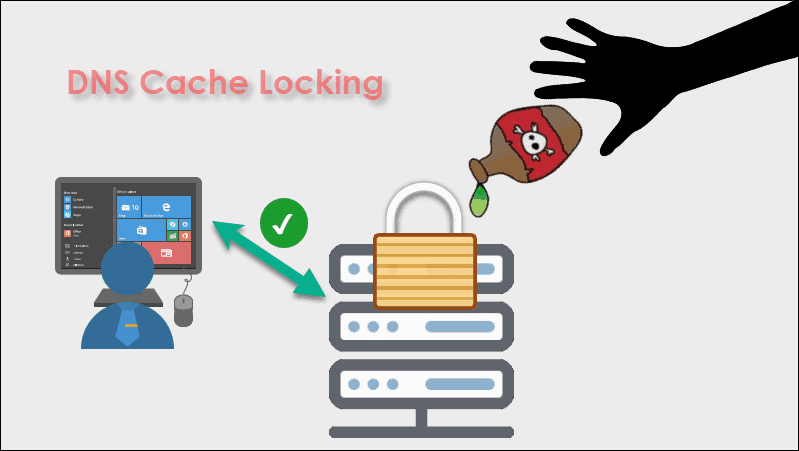
2: DNS Cache Lock
Every time a client makes a request, DNS locates the data and saves it in the cache for later use. The server can respond to the same queries more quickly because of this technique. By changing the data that is stored, attackers can take advantage of this functionality.
Locking the DNS cache is a step after enabling DNS to debug logs. When the cached data can be modified is determined by this feature. The server retains lookup data for the time period specified by the TTL (time to live).
The information can be overwritten before the TTL expires if cache locking is not enabled. Attacks using cache poisoning are made possible by this.
Cache locking could be activated by default depending on the operating system. The cache locking scale can reach 100%. For 70% of the TTL, overwriting the data is not allowed when the value is set to 70. Cache locking is set to 100, which prevents altering the cached data until the TTL has passed.
3: Block harmful domain requests by filtering DNS requests
Users can be prevented from visiting a website or domain by using DNS filtering. If a domain is known to be malicious, that is the major justification for blocking name resolution for that domain.
Any contact between a client and a DNS server is terminated when the client sends a query for a blocked website.
DNS filtering significantly lowers the likelihood that malware and viruses may enter your network. A client cannot access a bad page, hence there are very few risks that can slither within your architecture.
Your IT personnel won’t have to spend their entire day eradicating infections thanks to this method. A domain may be blocked by an organization for reasons of productivity or business policy in addition to security.
Social media, gaming, pornography, video streaming sites, and other websites may be on the list of forbidden domains. A user, a group, or all users’ access can be blocked using DNS.
DNS filtering is a basic feature of contemporary software security and firewall programs. Some of these products include lists of undesirable domains that are frequently updated. You may automate DNS filtering and avoid adding new entries manually by using a ready-made software solution.
4: Use DNSSEC to verify the integrity of DNS data.
Clients are guaranteed to obtain accurate answers to their requests thanks to Domain Name System Security Extensions (DNSSEC). By using DNSSEC to digitally sign DNS data sent to name servers, data integrity is achieved.
A DNS server includes a digital signature with the response when an end user sends a query. Clients are so certain that they received accurate information in response to their requests.
Attacks on the DNS protocol can be repelled with the help of this extra security layer. DNS spoofing attacks and cache poisoning are effectively avoided since DNSSEC provides data integrity and origin authority.
What are Some Best Practices When Creating Internal DNS Namespaces? Customers may thus be sure they are going to the pages they are meant to go to.
5: Make Access Control Lists configurations
Another method of defending DNS servers against unauthorized access and spoofing attacks is through access control lists (ACL). Your principal DNS should only be accessible to system administrators and IT staff.
Just the intended staff can communicate with your servers by configuring ACLs to permit inbound connections to a name server from only certain hosts. ACLs must also specify which servers are allowed to transfer zones.
Attackers may use alternative DNS servers to issue zone transfer requests in an effort to learn more about your zone configuration. An attacker cannot access zone information if all zone transfer requests through secondary servers are blocked. This configuration keeps others from learning about how you’ve set up the internal network.
Conclusion
Your infrastructure’s security and DNS architecture are both areas that may always be strengthened. Threats are always present, waiting to take advantage of weak spots in your IT infrastructure.
Here at Arzhost, we discuss What Are Some Best Practices When Creating Internal DNS Namespaces? But if you adhere to the advice provided in this manual, you will take care of the crucial elements your DNS infrastructure requires to remain safe and dependable.